Salesforce Single Sign-On Error: Network users can access all permitted network resources with a single sign-on, eliminating the need to log in to each resource individually. Instead of having separate user passwords controlled by Salesforce, single sign-on enables you to validate usernames and passwords against your corporate user database or other client applications.

Salesforce is among the many contemporary workplace apps that depend on Single Sign-On (SSO). With just one set of credentials, users can access numerous applications. However, SSO integration with Salesforce might have problems, just like any other technology. We’ll examine typical Salesforce Single Sign-On issues, their causes, and successful troubleshooting techniques in this blog post.
Table of Contents
ToggleAn alternative approach to Salesforce Single Sign-On error implementation
In Salesforce, there are three methods available to accomplish this.
- Authorized delegation
- Authentication via Federation: IDP-Initiated SAML, SP-Initiated SAML
- OpenID Connect
Install a Salesforce Single Sign-On for Two Salesforce Organisations
One Salesforce organisation must be set up as the service provider and the other as the identity provider in order to create a single sign-on between the two.
Determine the provider (IDP): One reliable source that enables you to use single sign-on (SSO) to access other websites is an identity provider.
Provider of services (SP): A website that hosts apps is called a service provider.
How to configure a single sign-on between two Salesforce accounts
How to configure a single sign-on between two Salesforce organisations:
- Enable My Domain in both Salesforce Organisations. (In Both Organisations)
- Activate Identity Providers (IDP Organisations) Obtain Certificates Obtain Metadata
- Configuring a Single Sign-On (SP Org): Set up the SAML Sigle Sign-on, upload the metadata file, and Upload the Certificate of Identity Provider.
- Make a linked application (IDP Org).
- Modify my domain’s authentication configuration in SP Org.
- Try out your setup: Configure Users in IDP and SP
Step 1: Enable My Domain in both Salesforce Organisations. (In Both Organisations)
In the new Salesforce org, my domain ought to be activated by default already. Enable it from “My Domain” if it isn’t already.
Step 2: Activate Identity Providers (IDP Organisations) Obtain Certificates Obtain Metadata
After creating the certificate, enable identity providers. Go to Identity Provider after logging into your IDP organisation. Identity Provider under Setup -> Security Controls.
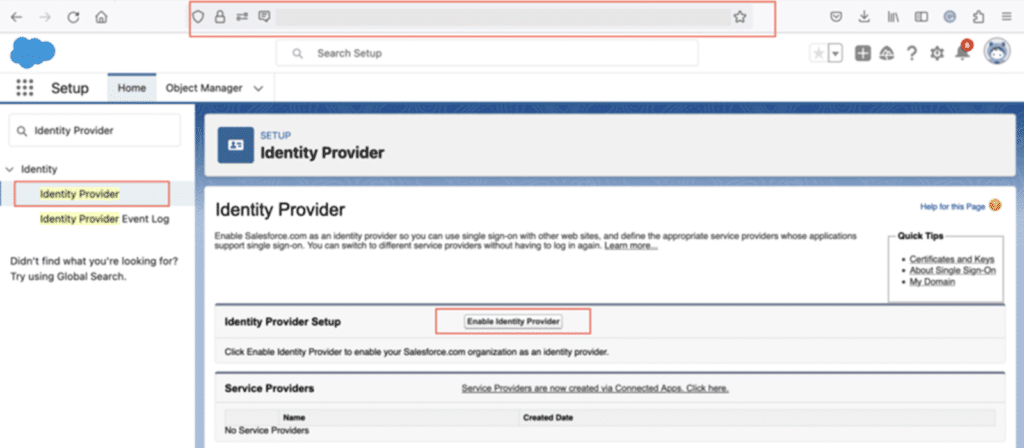
Next, select “Enable Identity providers” from the menu. Next, select the certificate that Salesforce.com employs for service provider communication.
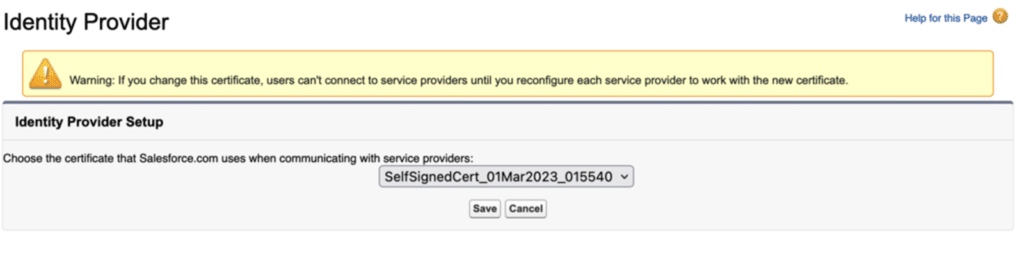
Click on save button.
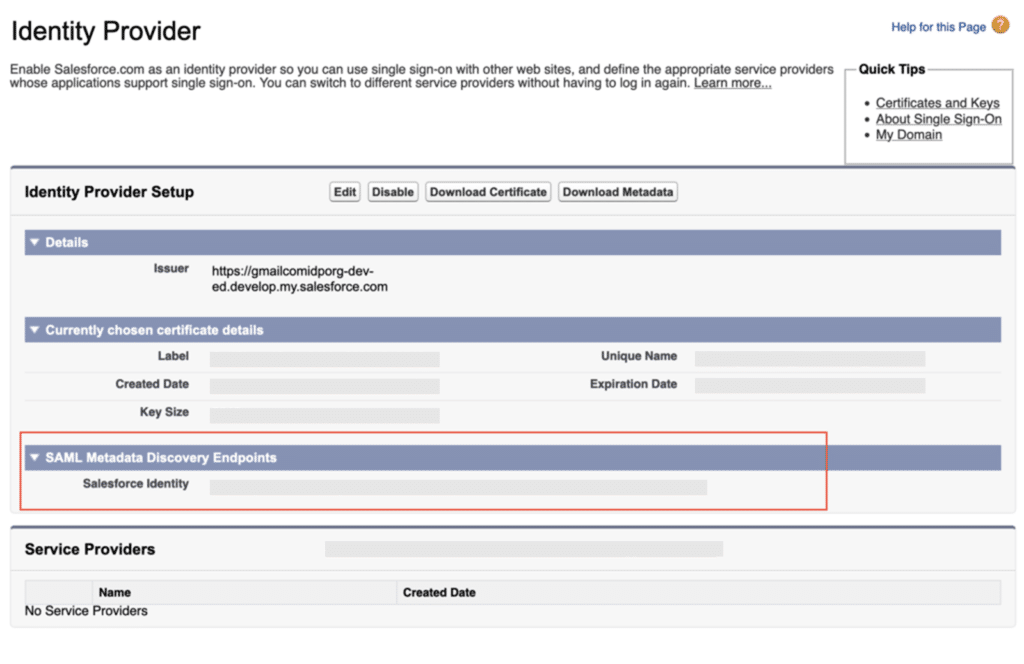
Step 3: Configuring a Single Sign-On (SP Org): Set up the SAML Sigle Sign-on, upload the metadata file, and Upload the Certificate of Identity Provider.
Activate Single Sign-on and SAML. Go to “Setup > Identity > Single Sign-On Settings” and choose the option labelled “SAML Enabled.”Next, select “Enable Identity providers” from the menu. Next, select the certificate that Salesforce.com employs for service provider communication.
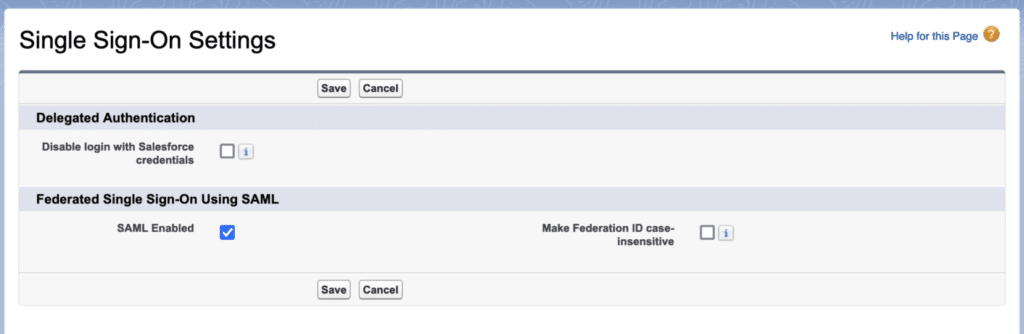
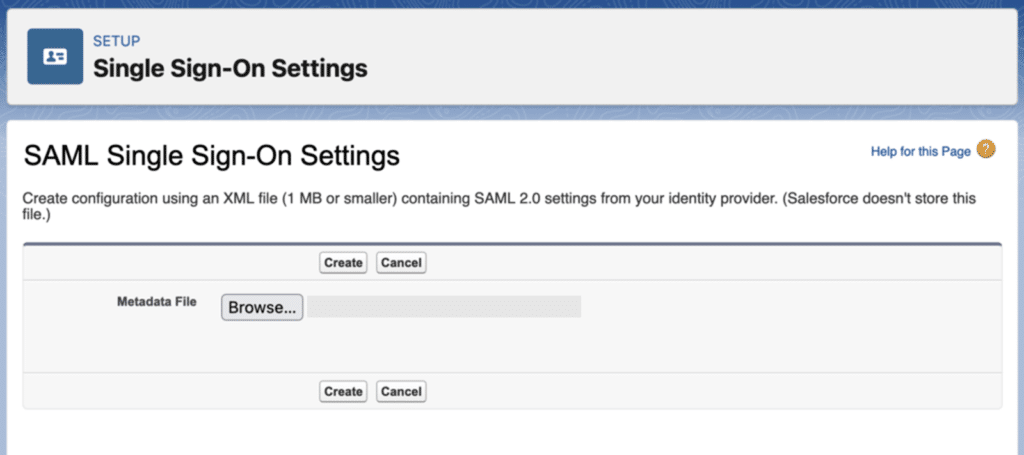
Set up SAML Single Sign-on and upload the metadata file.
Give the details of the SAML Single Sign-On setting now. The “New from Metadata File” button allows you to upload a Metadata file that you can utilise from step 2.2.
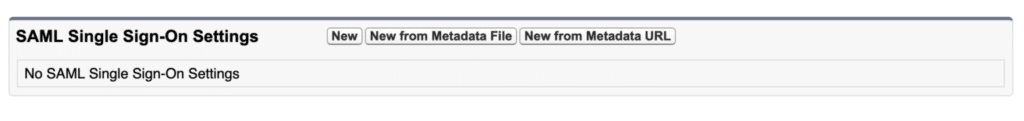
To upload the Metadata file, choose “New from Metadata File.”
Update the settings and upload the Identity Provider Certificate.
We download the Identity Provider Certificate from 2.1, update the SAML Single Sign-On Settings, upload it, and choose “Assertion contains the Federation ID from the User object.”

Take note of the login URL and entity ID from this page. Similar will be used in the IDP org Connected App.

Step 4: Make a linked application (IDP Org).
Now, enter your IDP org once more. And use the next step to establish a connected app.
- Setup -> App Manager -> New Connected App is where you create connected apps.
- Now give every necessary detail. Make sure you carry out the following procedure on your connected app.
- Activate SAML and enter the entity ID (use the entity ID from step 3).
- (Login URL from Step 3) ACS
- Federation ID should be the Subject type.
- Identity Provider Certificate as Label Name
- Once the Connected app is ready, proceed. Select Manage from the menu. The profile from the associated list is then added.

Step 5: Modify my domain’s authentication configuration in SP Org.
Go to SP org now and select My Domain from the setup menu. Select the IDP org in the Authentication service after editing the Authentication configuration setting.
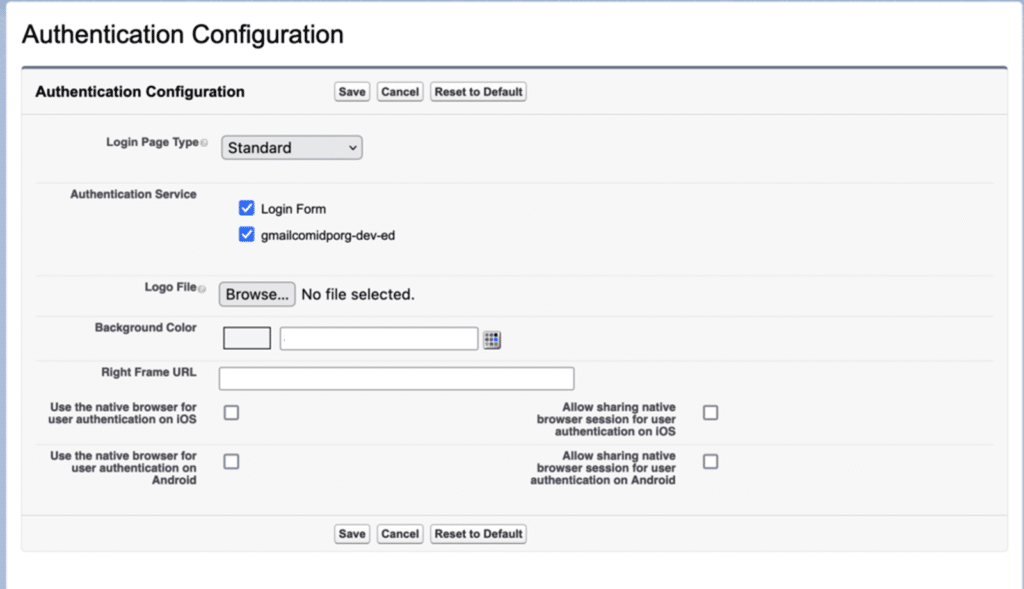
Step 6: Try out your setup: Configure Users in IDP and SP
Make a user with the same “Federation ID” in both organisations.
SAML Flow Testing Started by the Service Provider
Click the “Log in with IDP-org” button on your Service Provider org page.

You’ll be directed to the IDP org for validation. Your login and passphrase.
URL for IdP-Initiated Login
Take note of the Identity Provider Organization’s IdP-Initiated Login URL. Open in a different tab, too. You will be directed to SP org.
Methods for Fixing a Salesforce Single Sign-On Error
Every issue presents an opportunity to learn something new, and every Salesforce administrator I’ve ever encountered enjoys expanding their knowledge of the platform. When we own our mistakes and decide to employ something we didn’t know how to accomplish, we’re frequently the first to do so. No matter how long you’ve been using Salesforce, there’s always something new to learn, especially with the frequent releases (and release notes the length of a short novel!).
You may quickly and easily troubleshoot the mistake with the help of this guide, ensuring that your users are signed in and operating as efficiently as possible.
Best Practices for Troubleshooting Salesforce Single Sign-On Error
Verify the Salesforce setup: Make sure the settings for Salesforce SSO adhere to the guidelines provided by your identity provider.
Examine SAML Assertions and Responses: Verify that the formatting, signatures, and attribute values of SAML assertions and responses are valid.
Verify Certificates: Ascertain the validity and proper configuration of the certificates used to sign SAML assertions and answers.
Monitor Logs: For thorough error messages and information about the SSO procedure, review the audit and Salesforce login logs.
Engage Support: Ask your Identity Provider or Salesforce support for help if you need help figuring out the problem.
Terminology for Single Sign-On
These terms cover SAML-enabled SSO.
- Identity Providers and Service Providers can exchange identity attributes and confirm identities using XML thanks to the Security Assertion Markup Language (SAML), an open standard.
- Identity Providers (IDPs) – An application that may verify identification and authentication attributes to a service provider and authenticate a user (i.e., enable login).
- Service Provider (SP) – An application that relies on an Identity Provider for user authentication and grants access to restricted resources or functionalities to the user
- The section of the SAML response that verifies the authenticated user’s identity attributes is known as the SAML assertion.
- The structured XML message that a service provider sends to an identity provider to identify itself and request user authentication is known as a SAML request.
- SAML Response: The Identity Provider’s XML message to the Service Provider in which it identifies itself as the issuer, reports the outcome of the authentication attempt, and, if possible, includes the SAML Assertion (which is usually signed with the Identity Provider’s certificate).
Conclusion
One effective feature that improves security and expedites user access is Salesforce Single Sign-On. That being said, mistakes will inevitably occur. Through comprehension of typical mistakes and adherence to recommended procedures for debugging, you may guarantee a seamless SSO integration with Salesforce and offer a flawless user experience.
Furthermore important are expertise and aggressive troubleshooting. Understanding the causes of common problems, like false claims and incorrect identity provider configurations, enables organizations to identify and resolve authentication problems quickly.
Assuring a smooth and safe Single Sign-On experience for users within the Salesforce ecosystem may be achieved by streamlining the integration process through the use of best practices, such as rigorous configuration validation, careful log monitoring, and prompt support when needed.




